
Agentless security for your infrastructure and applications - to build faster, more securely and in a fraction of the operational cost of other solutions

hello@secopsolution.com

In the world of cybersecurity, acronyms can feel like a different language. Professionals often come across CVSS, CVE, and CWE while assessing vulnerabilities, reading security advisories, or managing patch cycles. Although these terms are closely related, they serve different purposes in the vulnerability management ecosystem.
If you’ve ever wondered how these three fit together, this blog will break them down in detail and show how they complement each other.
Before diving into definitions, it’s important to understand the bigger picture: cybersecurity is not just about finding vulnerabilities but also about classifying, prioritizing, and remediating them effectively.
Together, they form the foundation of modern vulnerability management.
CVE is essentially the dictionary of cybersecurity vulnerabilities. Each known vulnerability gets a unique identifier called a CVE ID.
Example:
CVE-2017-0144 refers to the EternalBlue vulnerability in Microsoft SMB protocol, famously exploited by the WannaCry ransomware.
Without CVEs, different vendors might describe the same flaw differently, causing confusion. CVE makes vulnerability tracking consistent and universal.
CWE describes the root cause of vulnerabilities. Instead of focusing on a single instance like CVE, CWE provides a taxonomy of common coding and design flaws that lead to vulnerabilities.
Example:
CWE-79: Improper Neutralization of Input During Web Page Generation (Cross-Site Scripting).
CWE-89: SQL Injection.
If CVE tells you what went wrong in a particular case, CWE tells you why such issues keep happening.
CVSS is the measurement system used to determine the severity of a vulnerability. It translates technical details into a numerical score (0.0 to 10.0), making it easier for organizations to prioritize remediation.
Example:
EternalBlue (CVE-2017-0144) had a CVSS v3 base score of 8.1 (High), but in many environments, its impact was closer to 10.0 (Critical) because of its worm-like exploitability.
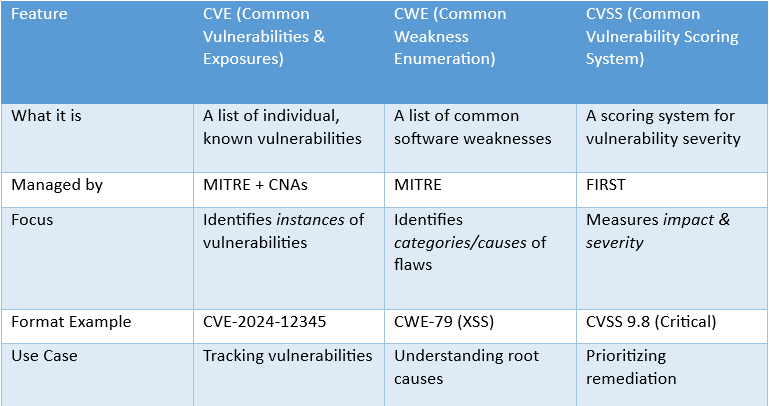
Think of CVE, CWE, and CVSS as different parts of the same puzzle:
Example Workflow:
This chain provides a complete picture: identification, cause, and risk level.
Without this ecosystem, vulnerability management would be chaotic and fragmented.
Cybersecurity is full of acronyms, but CVSS, CVE, and CWE form the backbone of vulnerability communication and prioritization.
Together, they ensure that organizations worldwide speak the same language when it comes to vulnerabilities, helping us respond faster and more effectively to threats.
"Understanding CVSS, CVE, and CWE is the first step toward better vulnerability management. Start by mapping your current vulnerabilities with their CVE IDs, checking for CWE patterns in your codebase, and using CVSS to prioritize patching. This structured approach can save your organization from the next major breach."
SecOps Solution is a Full-stack Patch and Vulnerability Management Platform that helps organizations identify, prioritize, and remediate security vulnerabilities and misconfigurations in seconds.
To learn more, get in touch.