
Agentless security for your infrastructure and applications - to build faster, more securely and in a fraction of the operational cost of other solutions

hello@secopsolution.com

In today’s cybersecurity landscape, compliance is no longer optional—it’s mandatory. From HIPAA and PCI DSS to ISO 27001 and NIST frameworks, organizations must prove they are maintaining a strong security posture. One of the most critical aspects of compliance is patch management—ensuring all systems, servers, and applications are updated with the latest security patches.
But simply patching isn’t enough. Auditors want proof. That’s where patch compliance reports come into play. These reports document your patching activities, show your adherence to compliance standards, and help you stay prepared for internal and external audits.
In this blog, we’ll cover:
A patch compliance report is a structured document that provides visibility into the current patch status of your IT assets. It shows whether your systems are up to date, highlights missing patches, and demonstrates compliance with industry regulations.
Auditors use these reports to validate that your organization has:
An effective report should include the following sections:
Here’s a simple structure you can use:
1. Report Header
2. Executive Summary
3. Patch Compliance Status (Table)
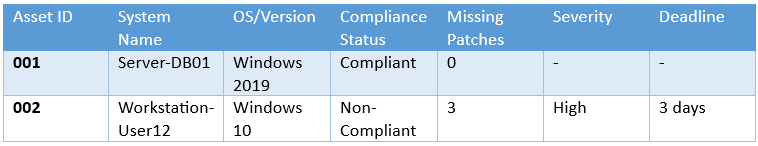
4. Vulnerability & Patch Risk Breakdown
5. Compliance Mapping
6. Exceptions & Justifications
7. Next Steps
Manually generating reports can be time-consuming and error-prone. Modern patch management solutions automate compliance reporting with real-time dashboards and exportable reports.
Some common tools include:
SecOps Solution offers a next-gen approach to patch management with features built specifically for compliance-driven organizations. With its lightweight, agentless technology, it scans your infrastructure, detects missing patches, and generates audit-ready compliance reports.
Key Benefits:
With SecOps Solution, organizations can walk into audits with confidence, knowing they have clear, structured, and regulator-friendly patch compliance reports at their fingertips.
Patch compliance reports are more than just paperwork—they’re your proof of cybersecurity diligence. With the right template, automated tools, and smart patch management solutions like SecOps Solution, organizations can simplify audits, stay compliant, and strengthen their overall security posture.
Instead of scrambling before audits, make compliance reporting an ongoing, automated process. That way, when auditors arrive, your only task will be to hand them a ready-to-go report.
SecOps Solution is an agentless patch and vulnerability management platform that helps organizations quickly remediate security risks across operating systems and third-party applications, both on-prem and remote.
Contact us to learn more.