
Agentless security for your infrastructure and applications - to build faster, more securely and in a fraction of the operational cost of other solutions

hello@secopsolution.com

In modern enterprise environments, vulnerability scans rarely return a manageable list. Instead, security teams are overwhelmed with dashboards full of red — hundreds or even thousands of findings marked “Critical.”
At first glance, this seems helpful. Critical means urgent, right?
But when everything is critical, nothing truly is.
Most organizations rely on scanning tools such as:
These tools assign severity scores using the Common Vulnerability Scoring System (CVSS).
A vulnerability with a CVSS score between 9.0 and 10.0 is labeled Critical.
The issue?
CVSS measures theoretical severity — not your organization’s actual risk.
It does not consider:
As a result, security teams end up treating thousands of vulnerabilities with the same urgency — leading to:
CVSS was designed to provide a standardized technical severity score. It answers:
“How bad could this vulnerability be in theory?”
But risk-based prioritization should answer:
“How likely is this vulnerability to cause real damage to our organization?”
Here’s what CVSS does not capture:
A CVSS 9.8 vulnerability with no public exploit may pose less immediate risk than a CVSS 7.5 vulnerability that has active exploitation.
If threat actors are actively weaponizing a vulnerability, its practical risk skyrockets — regardless of CVSS.
A vulnerability on:
Business context matters.
Is the system:
Exposure dramatically changes risk.
Effective prioritization requires combining technical severity + business impact + threat intelligence.
Let’s break down a smarter framework.
Not all systems are equal.
Categorize assets into tiers:
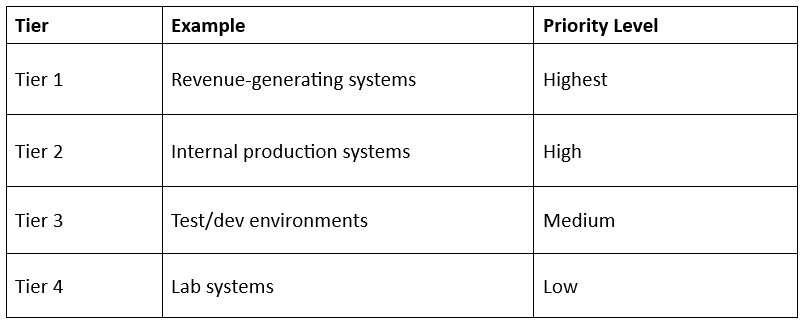
A CVSS 8.0 vulnerability on a Tier 1 system may be more urgent than a CVSS 9.5 on a Tier 4 system.
The Exploit Prediction Scoring System (EPSS) estimates the likelihood that a vulnerability will be exploited in the wild.
High CVSS + High EPSS = Immediate attention
High CVSS + Low EPSS = Monitor strategically
This dramatically reduces noise.
Internet-facing vulnerabilities should move to the top of your remediation queue.
Ask:
Exposure increases attacker opportunity.
Prioritize vulnerabilities that:
For example, organizations often monitor advisories from:
If a vulnerability appears in active exploitation alerts, elevate it immediately — regardless of raw CVSS.
Ask:
If strong controls exist, risk may be temporarily reduced.
Go beyond technical risk. Map vulnerabilities to:
A vulnerability affecting PCI environments carries far more impact than one in a non-sensitive internal tool.
Instead of fixing individual CVEs, group vulnerabilities by:
Fixing one patch often eliminates dozens of vulnerabilities.
This shifts teams from reactive CVE chasing to structured remediation cycles.
Manual prioritization doesn’t scale.
Modern vulnerability management platforms combine:
This enables security teams to focus on what truly reduces risk — instead of chasing thousands of red alerts.
Instead of:
Track:
These metrics align security with business outcomes.
When vulnerability dashboards are flooded with “Critical” alerts, organizations don’t need more data — they need clarity.
That’s where SecOps Solution transforms the approach to vulnerability management.
Instead of relying purely on CVSS-based severity scoring, SecOps Solution applies a risk-first methodology
SecOps Solution correlates vulnerabilities with:
This ensures that remediation teams focus on vulnerabilities that create real operational risk, not just high theoretical scores.
The future of vulnerability management isn’t about fixing more CVEs.
It’s about fixing the right ones first.
By moving from severity-based to risk-based prioritization, organizations can:
When everything looks critical, the real competitive advantage is clarity.
SecOps Solution is an agentless patch and vulnerability management platform that helps organizations quickly remediate security risks across operating systems and third-party applications, both on-prem and remote.
Contact us to learn more.